Security at AddSecure
At AddSecure security is embedded in everything we do. We take security, safety, and privacy seriously.
We work proactively to support a strong security culture and awareness among employees at all levels, not only among our highly skilled IT security professionals. Our culture and capabilities ensure the protection of our assets, resources, and operations from threats, harm, or misuse.
To establish a strong security culture in our organisation, we have taken the following measures:
Established security policies and procedures
Train all employees on security best practices
Encourage reporting of security incidents
Regularly assess security risks

Get ready for NIS2. Read our guide!
Our guide helps clairify the implications of NIS2 and offers a checklist as well as hands-on recommendations.
-
What is NIS2?
-
Which organisations does NIS2 apply to?
-
Checklist and recommendations
-
How AddSecure can help
IT and information security
Our IT strategy aims to support the overall growth strategy by increasing operational efficiency and customer satisfaction through digitalisation. However, risks deem to increase, the more digitised we get.
Information assets and information management form the basis for AddSecure’s core business. The information assets are protected through risk-based and structured information security processes against threats that could lead to loss, inaccessibility, alteration, or wrongful disclosure.
If the information is not adequately protected, it might have severe financial consequences, loss of public confidence, lost business opportunities, and could even lead to health and safety incidents. With this in mind, it is essential that our employees strive towards fulfilling our information security objectives.
Information is how we convey knowledge, and it is managed by a combination of people, processes, and technology. Some information assets are valuable to AddSecure. If some information is lost or incorrect it may have harmful consequences. Therefore, we strive to protect information so that it is:
- There when we need it (availability)
- Correct and not manipulated or destroyed (integrity)
- Only available to authorised individuals (confidentiality)
Activities included in the information security area are:
- Business analysis
- Security assessment (what to protect, protect against what, how to protect)
- Security roadmap (action points and responsible function)
- Continuous improvement
Security incident reporting
The security incident response process includes identifying an attack, understanding its severity, and prioritising it, investigating and mitigating the attack, restoring operations, and taking action to ensure it will not reoccur.
System management list
AddSecure has a system management model that aims to protect the investment of every IT system that has been developed and purchased. The objective is to have clear ownership of systems in production, to maintain knowledge, manage incidents according to our operations model and investment needs.
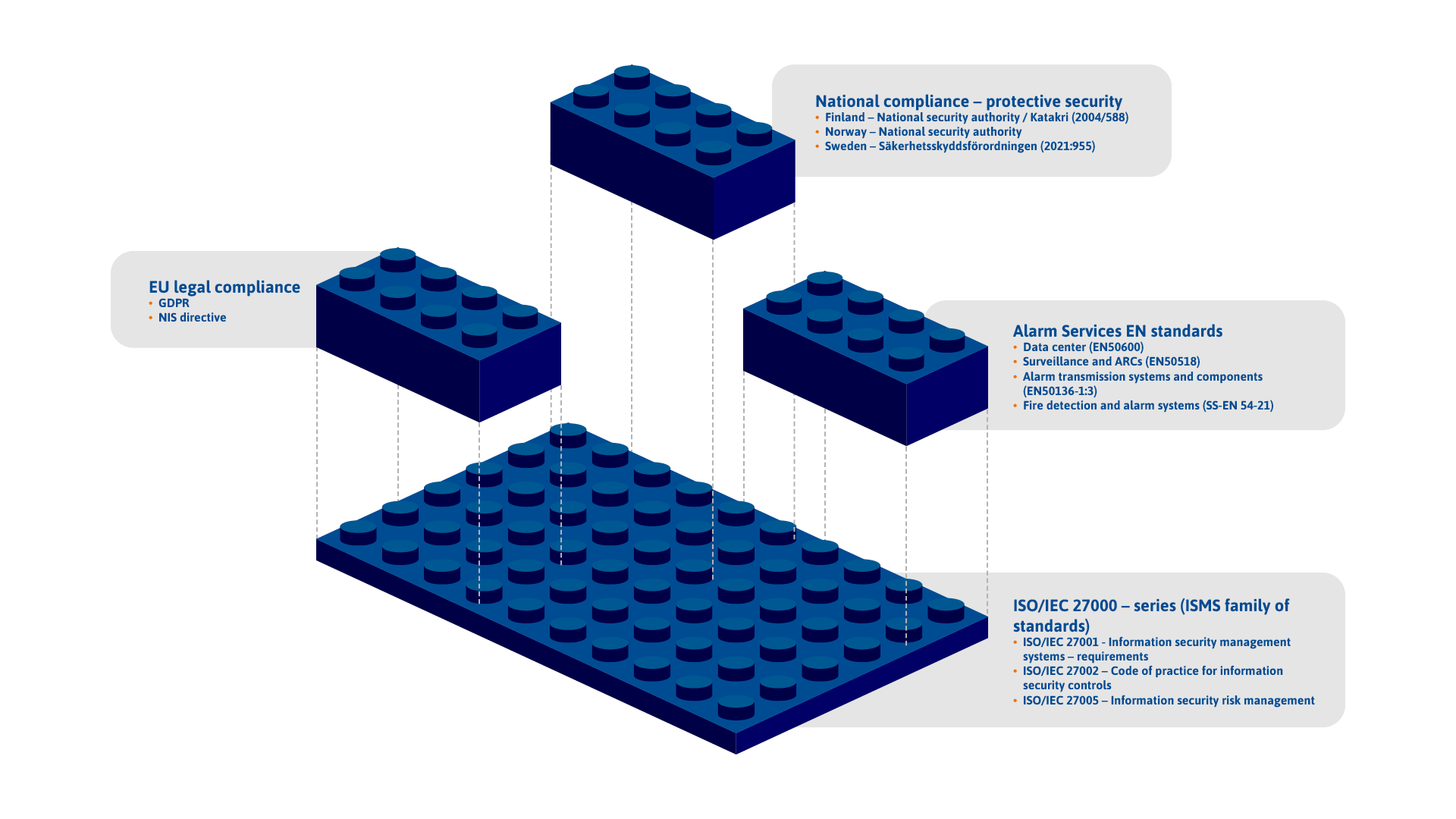
Protective security
There are increasingly high demands on protective security and protective security procurements which are of importance for the national security. At AddSecure we work continuously to ensure that laws and regulations that apply to protective security are complied with.
The national adaptation is covered on country level. See your local domain for more information.
The national protective security consists of three corner stones:

Information security
Organisations within vital sectors which rely heavily on information networks, for example utilities, healthcare, transport, and digital infrastructure, are identified by each member state as “operators of essential services” (OES). The OES are required to take appropriate and proportionate security measures to manage risks to their network and information systems, and are required to notify serious incidents to the relevant national authority.

Physical security
Physical security describes security measures that are designed to deny unauthorised access to facilities, equipment, and resources and to protect personnel and property from damage or harm, such as espionage, theft, or terrorist attacks.

Personal security
Personal security refers to protection against personnel who are not reliable working with sensitive data from a security perspective. Personal security consists of safety assessment and training in national security. An employment in a security-sensitive business is usually placed in a security class.
Contact
If you have an inquiry or want to learn more about security at AddSecure, please contact us.

Krister Tånneryd
Chief Operating Officer
[email protected]
Phone: +46 701 410 000